Two months ago, I got screwed on my main PC by a piece of malware called Windows Scan. I had planned on writing a small piece about my experience and the two and a half hours it takes to remove this fake antivirus program from my computer. One thing I had learned about it was exactly at what point I had set loose its payload on myself.
But, I had alot of work on my hands to do in a two day timeframe before going away for a couple of weeks so, I had never got around to writing this article. While I was gone, I encountered this same piece of garbage on my sister’s computer. And I found it in nearly the same way, by using Google Image Search. This time, however, I was wise enough from my previous experience to simply pull the plug from her computer without clicking another damn thing. Due to the way this malware functions, that was enough to keep this garbage from unleashing its payload on my sister’s machine and burning two and a half hours of my time at her place. Upon reboot, it was simply a matter of flushing her web browser’s cache to rid the machine of any potential remains.
Two days ago, I had another encounter with this crapware on my computer. There were several differences this time. For one, I was not clicking on any Google Image Search. In fact, I wasn’t actually doing anything with the computer at the moment of infection. I had Windows Update running and I was reading an article about cascading style sheet menus in another browser. I’d looked away from the computer screen for a few minutes altogether while concerning myself with something completely different. When I returned a few minutes later, here was this piece of crap beginning its run on my computer.
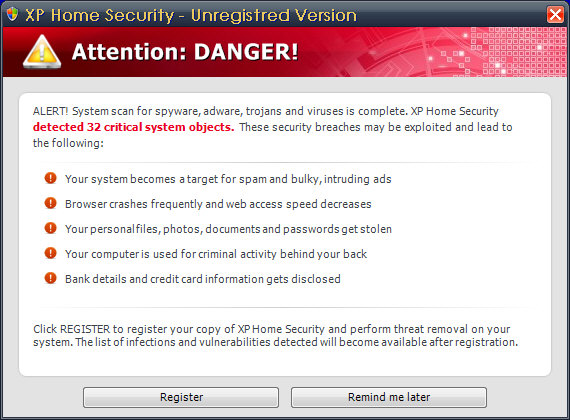

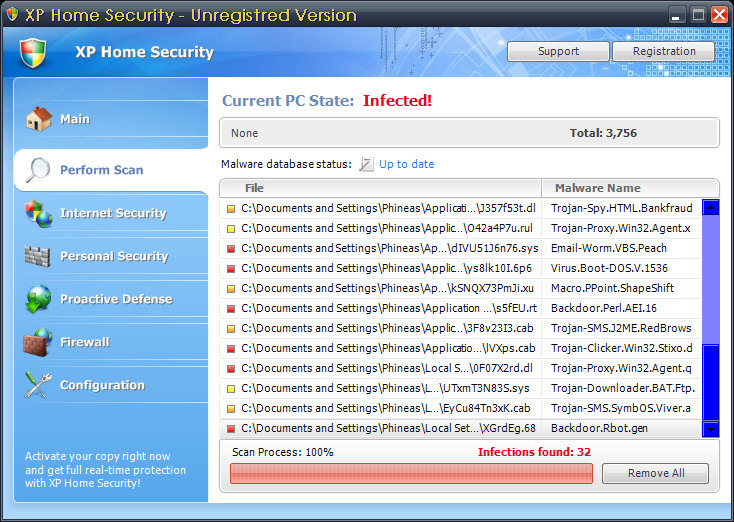
If you were to punch “Windows Scan” into Google search, you can come up with plenty more of the same thing. From these shots, you can see that this time, the malware has a different name, XP Home Security, but it’s still the same lameware crapola.
So, if I wasn’t actively clicking anything, and believe me, this crap launches pretty darn quickly, how did I contract the evilware again? Along with my attempts to cleanse my system of this, I did a bit of evidence gathering this time. By putting my forensic hat on, I may have sacrificed my ability to eliminate the beast without trashing my system. In fact, after my data mining, I made two attempts to reinstall the operating system on my computer. The second attempt because of the first’s failure. Yes, a hard drive format was required. Nothing like a clean install for that wake up feeling fresh-in-the-morning feeling is there?
I learned plenty this go around with this rotten piece of shit. I felt it pretty unlikely that the malware was contracted on Microsoft’s website while doing the Windows Update. I mean, that certainly would have been a hoot if I received malware from the mothership there but I don’t believe that was the cause. Rather, that browser window, which was the only other thing I had open on my system. Just a page I was reading while Windows Update was “getting it on”.
I’d installed the browser the day before this incident and I’ll admit that I didn’t fully know what I was doing with it yet. That browser was Google Chrome. I hadn’t had much experience with Chrome yet for a good reason. Until my previous bout with Windows Scan, I was running Windows 2000 Professional as my main system. Chrome requires XP or higher. That was the other pisser about reinstalling the operating system; my XP MCE ’05 installation was not very old at all!
Anyhow, the culprit in Google Chrome is a new one to me. Other browsers may do this as well, but I hadn’t run across it yet. Chrome does something called prefetch. What it means is content is downloaded ahead of time. In other words, documents are prefetched from links on web pages. The idea behind prefetching is similiar to a computer’s CPU cache coupled with branch prediction. If the next link I was going to click can be downloaded ahead of time, when I actually click on that link, the next document would present itself to me nearly instantaneously.
I don’t want to damn this idea as being stupid; I don’t think that it is. At least, I don’t think it is entirely stupid. Google Chrome’s implementation or the execution in this case is what I have a problem with. I’d had another window open in Google Chrome at the time of this data disaster. The window was a page by Google to teach about how the Internet and World Wide Web works in some pretty simple language. I had been reading it with a critical eye for my own grins and also as a potential guide to others I know who don’t really understand as much about the topic as I do.
If you’re interested in reading it in its entirety, simply install Google Chrome and follow the pages that load up in the original tabs, it’s all there. But for me, in the course of reading their schtick with my critical eye, I saved a page of it prior to moving on when I came across some statements I found issue with.
Click this one here to see the excerpt I saved.

Keep in mind; I saved this prior to my little malware disaster!
I have more than one issue with this page out of Google’s book. I’ll stick with the statement number four as my bone to pick at in this monologuing. This is the one that is directly relevant to this article here. I disagree with the premise of Google’s claims of ethereal security. When I had a college course once, the instructor asked what’s the best way to keep a computer from getting a virus? I was the only person in the class who was even close on the answer. The correct answer was to not plug the computer in at all (not power it on!). My answer was to not connect the cable to the network. He liked my answer enough to equate my thinking on this matter to his correct answer. And that’s why I have issue with Google’s claims of their model being “safer”.
I even have a further issue with Google’s technology when it comes to this aggressive prefetching of Web content in Chrome. I did find a worthwhile guide to disabling this “It’s not a bug; it’s a feature!” on the Web. If you’re going to use Google Chrome, I highly recommend reading it first. As for me, my reasons for installing Chrome were simply for having another browser to test rendering of pages I author on. When I can contract computer AIDS with it in less than 24 hours without clicking a damn thing, I’ll have to say that Google isn’t very good with browser security.
But this experience doesn’t stop for me here. New lesson about prefetching learned the hard way extremely cemented in my mind, I moved on to the actual malware at hand. The first times that I came across this Windows Scan, I was actually running antivirus software. Avast! is free and I had the attitude that you sometimes get what you pay for in that Avast! did actually identify the malware but only after the payload was delivered!
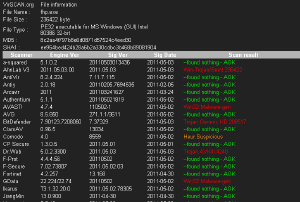
So, having wasted the better portion of a day doing the forensics and completely rebuilding my system (a task I’m getting much quicker with due to repetitive habit!), I set out to find out what kind of shielding I could find on the Web from this monstrosity. What I needed was a place to upload my captured malware to test antimalware detection capability. I found more than what I was looking for at VirSCAN.org. The report I got from my little file was very disturbing:
Many of these programs I’d never heard of before, which isn’t too surprising. What’s disturbing is that only eight anti-virus/anti-malware programs out of a battery of 37 actually correctly detected my caged executable. The Comodo program’s heuristic analysis suspected something was amiss, so maybe that makes nine programs. But this malware existed at least as early as January 2010! Furthermore, it’s a widely documented problem; just punch Windows Scan into a Google search and you’ll get volumes back from other people who had experienced this rotten apple.
Look at this list! Neither McAfee nor Symantec (Norton AV) identified this. Both titles I’ve had no confidence in for over ten years. Trend Micro and Kaspersky didn’t detect it either, both of these I’ve actually paid to run on my computer at different times in the last ten years! But then you look at who did identify this malware and that list is surprising too. Microsoft?!